IT SECURITY
Our platform is updating the vulnerability identifying capabilities every minute and AI
We focus on bringing value and solving business challenges through the delivery of modern IT Security and solutions
Security is essential for any given organization, threat remain the same for all organizations and hackers don’t care if you are a small or big companies. You may be a direct target or advisories use your network as a pivot point to attack other networks. A successful attack impacts the organization’s reputation and It is hard to bring back the customers at the same time impact creating a big financial burden that affects the future of the company ‘s growth. Security becomes essential to success in your business. Now, the critical objective of any organization across the continental is “protect the customer data”. Our platform approach is unique and creates a possible workflow to test every single page of the customer application.
Find Out MoreFirst Step
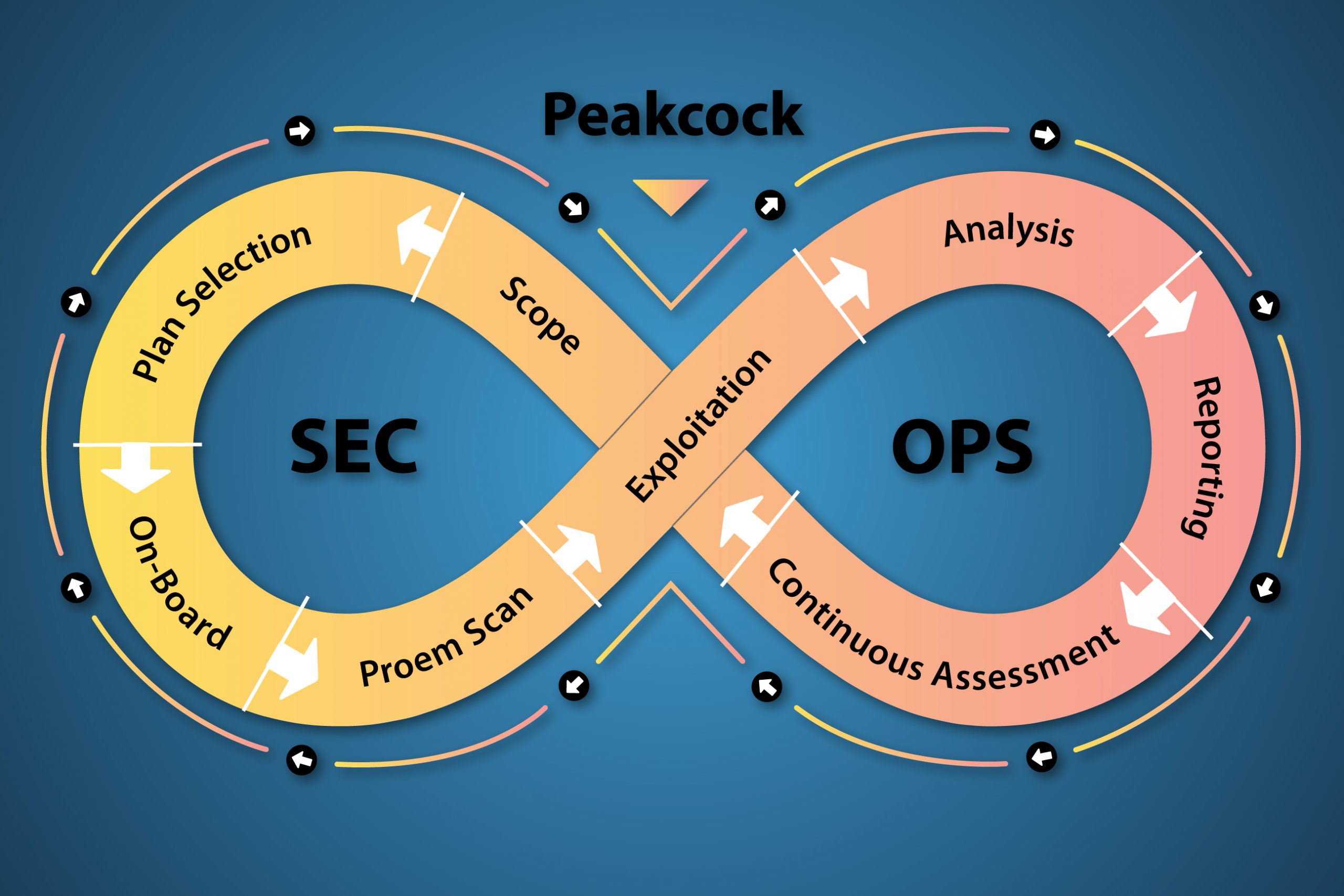
Choose the Package and Start the trail
Second Step
Update the Target Scope
Third Step
Review the Reports & Dashboard
We offer Best in class cyber security services
Vulnerability Disclosure Program
With increasing technologies and platforms, the rise of cyber-attacks has become threefold. It is important to maintain proper cyber hygiene to avoid attacks on the organization’s assets.
READ MORE +Audit & Accreditation
CyberOne is an independent audit & accreditation firm helping customers to plan, develop, and implement compliance & certification programs and we will conduct independent & certification audits.
READ MORE +Cloud Security Assessment
Identify potential weakness which can be exploited to perform attacks such as sensitive data exposure
READ MORE +Threat And Vulnerability Management
Vulnerability management services provide critical visibility across all your IT assets .where they are most vulnerable. From there, our team will prioritize remediation tactics to further improve your security posture
READ MORE +IoT Security
9IoT security is the practice that keeps your IoT systems safe. IoT security tools protect from threats and breaches, identify and monitor risks and can help fix vulnerabilities. IoT security ensures the availability, integrity, and confidentiality of your IoT solution.
READ MORE +DevSecOps
DevSecOps as a Service will help you automate the implementation of threat modeling to identify potential threat vectors and attack
READ MORE +Red Teaming
Perform a comprehensive adversary simulation to measure your company cyber security posture
READ MORE +Bug Bounty
Bug bounty programs help organizations to identify potential vulnerabilities on critical assets at a faster pace
READ MORE +LET'S TALK ABOUT YOUR BUSINESS CYBER SECURITY NEEDS
TESTIMONIALS
Our Client Voices
It is great working with CyberOne Red Team, they found the security issues and help to solve significant cyber security challenges. Their cost effective solution is good fit for SMB sectors
Peakcock is a real bug-bounty platform for the SMB sector
Thanks to CyberOne team to protect our application from targeted threats.
Peakcock is a promising VDP platform, and it is a cost-effective solution. Our cyber team taking advantage of the solution to meet the compliance requirement.

Container Security
Designed, implemented, and executed the container security program for a USA’s largest transportation company.

Bug-Bounty Program
Designed, implemented, and executed the container security program for a USA’s largest transportation company.